In today’s complex digital environment, compliance is no longer just a regulatory checkbox—it is a cornerstone of business credibility. Organizations across industries must demonstrate that they can protect sensitive data, prevent unauthorized access, and maintain strict security protocols. Achieving this requires adopting advanced authentication solutions that align with global regulatory standards and provide users with secure, seamless access to systems.
By implementing a modern authentication solution, businesses not only strengthen their defense against cyber threats but also ensure compliance with laws such as GDPR, HIPAA, PCI DSS, and other regional frameworks designed to safeguard privacy and data integrity.
1. The Growing Need for Compliance in a Digital World
Regulators worldwide are imposing stricter guidelines on how organizations manage data security. From financial records to patient information, companies must prove that they can prevent breaches and unauthorized access. Non-compliance can lead to hefty fines, reputational damage, and customer distrust. Authentication stands at the core of compliance because it controls who can access what, and under which circumstances.
2. Role of Authentication Solutions in Regulatory Alignment
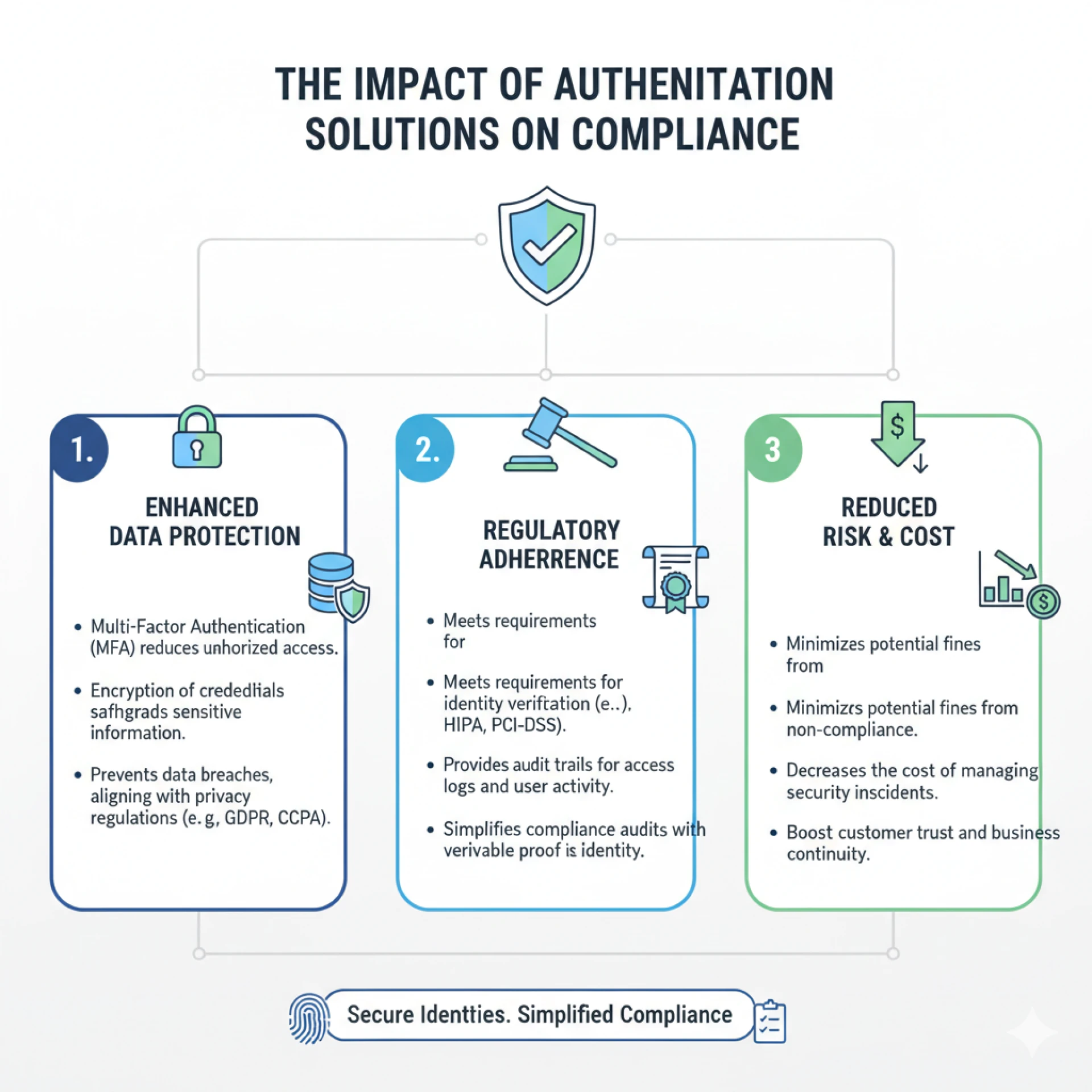
Authentication solutions provide a foundation for compliance by:
- Ensuring identity verification: Strong, multifactor methods validate user identities with high assurance.
- Meeting data protection laws: By encrypting and securing login processes, they reduce risks of exposure.
- Providing audit trails: Authentication systems track access events for regulatory reporting and audits.
- Supporting industry frameworks: Solutions are designed to align with standards such as ISO 27001, NIST, and SOC 2.
These capabilities make them indispensable for organizations under regulatory oversight.
3. Passwordless Authentication and Compliance
Password-based systems are often the weakest link in compliance efforts. Password reuse, phishing, and breaches compromise security, exposing organizations to penalties. Passwordless methods such as biometrics, security keys, and cryptographic authentication eliminate reliance on vulnerable credentials, offering:
- Phishing resistance
- Fewer attack surfaces
- Improved access controls
This not only enhances security but also ensures adherence to compliance requirements centered on data privacy and strong authentication.
4. Compliance Benefits Beyond Security
Investing in robust authentication solutions brings additional compliance-related advantages:
- Reduced legal exposure: Stronger authentication minimizes liability in case of a breach.
- Customer trust: Clients are more willing to engage with organizations that visibly prioritize security.
- Global scalability: Solutions can adapt to regional compliance variations, making international operations smoother.
The alignment between compliance and security fosters both operational stability and market credibility.
5. Preparing for Future Compliance Demands
Regulations evolve as cyber threats change. Authentication solutions must adapt accordingly by offering flexibility, scalability, and future-ready technologies. Emerging standards, such as zero trust architecture, are already influencing compliance mandates. Organizations that adopt advanced authentication systems today will be better positioned to meet tomorrow’s requirements without costly overhauls.
Conclusion
Compliance is inseparable from security in the modern digital landscape. Strong authentication solutions not only protect organizations from cyber threats but also demonstrate a commitment to regulatory adherence, customer trust, and operational resilience. By choosing advanced systems like passwordless and FIDO-based methods, businesses can future-proof their compliance strategies while reducing risks and costs.



