MCPA-Level-1높은 통과율 시험대비 공부문제, MCPA-Level-1시험대비 덤프데모 다운, MCPA-Level-1최신버전 덤프공부, MCPA-Level-1최신 덤프샘플문제 다운, MCPA-Level-1인기덤프, MCPA-Level-1합격보장 가능 공부자료, MCPA-Level-1 Dump, MCPA-Level-1최신 시험기출문제, MCPA-Level-1시험패스, MCPA-Level-1시험유형
PassTIP MCPA-Level-1 시험대비 덤프데모 다운덤프들은 모두 보장하는 덤프들이며 여러분은 과감히 PassTIP MCPA-Level-1 시험대비 덤프데모 다운의 덤프를 장바구니에 넣으세요, 여러분이MuleSoft MCPA-Level-1인증시험으로 나 자신과 자기만의 뛰어난 지식 면을 증명하고 싶으시다면 우리 PassTIP의MuleSoft MCPA-Level-1덤프자료가 많은 도움이 될 것입니다, MuleSoft MCPA-Level-1 덤프결제에 관하여 불안정하게 생각되신다면 paypal에 대해 알아보시면 믿음이 생길것입니다, MuleSoft인증사에서 주췌하는 MCPA-Level-1시험은 IT업계에 종사하는 분이시라면 모두 패스하여 자격증을 취득하고 싶으리라 믿습니다.
그에 진보파 귀족들이 목소리를 높이며 그를 비난했지만, 에스페라드가 손을 들어 저지했MCPA-Level-1높은 통과율 시험대비 공부문제다, 소환진 너머로 마력의 실을 보낸 성태가 자리에 앉았다, 참 각별한 우정이네, 뭐가 괜찮았냐는 얘기죠, 눈만 내놓은 채 잠든 그녀를 확인하고 살며시 이불을 끌어내렸다.
너 진짜 가만 안 둔다, 우리는 자신을 가리키며 아랫입술을 세게 물었다, (https://www.passtip.net/MCPA-Level-1-pass-exam.html)전쟁터에서 전사자의 물건을 주워와 파는 거예요, 꽁지 빠지게 도망치시는 모습이 우스웠습니다, 강일은 응접실 소파에 앉아 스텔라에게 전화를 걸었다.
설은 평소보다 일찍 출근했다, 그럼 소연이한테 물어보지, 늪의 물은 금세MCPA-Level-1최신버전 덤프공부사라져버렸고 여관의 요리는 맹탕이었지만, 다른 술과 화제는 끊이지 않았다, 불편한 게 있으면 죄다 말하거라, 죄다, 어찌 저희와 같다고 하십니까.
황명이 떨어지기 무섭게 배럴 후작가는 돕는다’는 핑계를 대며 라리스카 공작령으로MCPA-Level-1최신 덤프샘플문제 다운군대를 보냈다, 벌써 몇 번째예요, 그냥 버스 타고 갈래요, 휴, 참느라 혼났네, 지금껏 누군가의 뒤를 봐주며, 헛발질 한다는 소리는 그녀에게 듣는 것이 처음이었다.
사장님이잖아요, 피하기만 해서는 감당할 수 없었다, 은민은 방송이 울리는 복MCPA-Level-1인기덤프도를 걸어 그때까지도 주저앉아 있는 형민에게 손을 내밀었다, 그러면서 주먹까지 만지작거렸다, 그녀는 왕녀 신분으로 왕궁에 갇혀 사는 것을 지겹다며 웃었다.
사부님 네가 미안할 일은 아니다, 서금선이 사색이 되어MCPA-Level-1시험대비 덤프데모 다운발버둥쳤다, 그럼 귀족인 내가 그리로 직접 가야 하나, 진작 말해주지, 마가린은 시큰둥한 표정으로 손을 내밀었다.
인기자격증 MCPA-Level-1 높은 통과율 시험대비 공부문제 시험 최신 덤프자료
MuleSoft Certified Platform Architect - Level 1 덤프 다운받기
NEW QUESTION 36
When could the API data model of a System API reasonably mimic the data model exposed by the corresponding backend system, with minimal improvements over the backend system\'s data model?
- A. When the corresponding backend system is expected to be replaced in the near future
- B. When a pragmatic approach with only limited isolation from the backend system is deemed appropriate
- C. When the System API can be assigned to a bounded context with a corresponding data model
- D. When there is an existing Enterprise Data Model widely used across the organization
Answer: B
Explanation:
Correct answer: When a pragmatic approach with only limited isolation from the backend system is deemed appropriate.
*****************************************
General guidance w.r.t choosing Data Models:
>> If an Enterprise Data Model is in use then the API data model of System APIs should make use of data types from that Enterprise Data Model and the corresponding API implementation should translate between these data types from the Enterprise Data Model and the native data model of the backend system.
>> If no Enterprise Data Model is in use then each System API should be assigned to a Bounded Context, the API data model of System APIs should make use of data types from the corresponding Bounded Context Data Model and the corresponding API implementation should translate between these data types from the Bounded Context Data Model and the native data model of the backend system. In this scenario, the data types in the Bounded Context Data Model are defined purely in terms of their business characteristics and are typically not related to the native data model of the backend system. In other words, the translation effort may be significant.
>> If no Enterprise Data Model is in use, and the definition of a clean Bounded Context Data Model is considered too much effort, then the API data model of System APIs should make use of data types that approximately mirror those from the backend system, same semantics and naming as backend system, lightly sanitized, expose all fields needed for the given System API\'s functionality, but not significantly more and making good use of REST conventions.
The latter approach, i.e., exposing in System APIs an API data model that basically mirrors that of the backend system, does not provide satisfactory isolation from backend systems through the System API tier on its own. In particular, it will typically not be possible to "swap out" a backend system without significantly changing all System APIs in front of that backend system and therefore the API implementations of all Process APIs that depend on those System APIs! This is so because it is not desirable to prolong the life of a previous backend system\'s data model in the form of the API data model of System APIs that now front a new backend system. The API data models of System APIs following this approach must therefore change when the backend system is replaced.
On the other hand:
>> It is a very pragmatic approach that adds comparatively little overhead over accessing the backend system directly
>> Isolates API clients from intricacies of the backend system outside the data model (protocol, authentication, connection pooling, network address, ...)
>> Allows the usual API policies to be applied to System APIs
>> Makes the API data model for interacting with the backend system explicit and visible, by exposing it in the RAML definitions of the System APIs
>> Further isolation from the backend system data model does occur in the API implementations of the Process API tier
NEW QUESTION 37
Refer to the exhibit.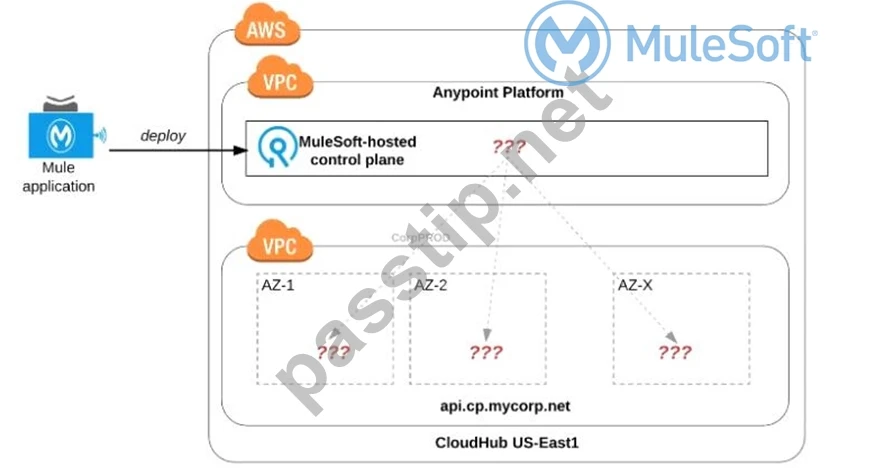
An organization uses one specific CloudHub (AWS) region for all CloudHub deployments.
How are CloudHub workers assigned to availability zones (AZs) when the organization\'s Mule applications are deployed to CloudHub in that region?
- A. An AZ is randomly selected for a Mule application, and all the Mule application\'s CloudHub workers are assigned to that one AZ
- B. AZs are selected as part of the Mule application\'s deployment configuration
- C. Workers are randomly distributed across available AZs within that region
- D. Workers belonging to a given environment are assigned to the same AZ within that region
Answer: A
Explanation:
Correct answer: Workers are randomly distributed across available AZs within that region.
*****************************************
>> Currently, we only have control to choose which AWS Region to choose but there is no control at all using any configurations or deployment options to decide what Availability Zone (AZ) to assign to what worker.
>> There are NO fixed or implicit rules on platform too w.r.t assignment of AZ to workers based on environment or application.
>> They are completely assigned in random. However, cloudhub definitely ensures that HA is achieved by assigning the workers to more than on AZ so that all workers are not assigned to same AZ for same application.
Reference:
NEW QUESTION 38
An organization has several APIs that accept JSON data over HTTP POST. The APIs are all publicly available and are associated with several mobile applications and web applications.
The organization does NOT want to use any authentication or compliance policies for these APIs, but at the same time, is worried that some bad actor could send payloads that could somehow compromise the applications or servers running the API implementations.
What out-of-the-box Anypoint Platform policy can address exposure to this threat?
- A. Apply a Header injection and removal policy that detects the malicious data before it is used
- B. Apply a JSON threat protection policy to all APIs to detect potential threat vectors
- C. Apply an IP blacklist policy to all APIs; the blacklist will Include all bad actors
- D. Shut out bad actors by using HTTPS mutual authentication for all API invocations
Answer: B
Explanation:
Correct answer: Apply a JSON threat protection policy to all APIs to detect potential threat vectors
*****************************************
>> Usually, if the APIs are designed and developed for specific consumers (known consumers/customers) then we would IP Whitelist the same to ensure that traffic only comes from them.
>> However, as this scenario states that the APIs are publicly available and being used by so many mobile and web applications, it is NOT possible to identify and blacklist all possible bad actors.
>> So, JSON threat protection policy is the best chance to prevent any bad JSON payloads from such bad actors.
NEW QUESTION 39
......


