As malicious email has multiplied during the COVID pandemic (Google reported on April 16th receiving 18M daily COVID- related malware & phishing attacks), it’s more important than ever for organizations to protect their employees from identity deception. DMARC enforcement adds an identity check to inbound email, but not all organizations with email gateways take advantage of it out of concern for blocking legitimate activity. Researchers identified a list of high-priority domains eligible for DMARC enforcement around which we recommend immediate action.
The tactics hackers use to break into computers and take control of accounts can vary, but one thing they all have in common is access to employee credentials. By implementing a security policy that restricts employees from using personal email accounts for business purposes and requiring employees to maintain their control over their work email addresses, you can help provide critical protection to your organization’s networks while keeping payrolls secure. Included in the analysis of nearly 50 million accounts, DMARC found attackers were increasingly using commercial email addresses with only the domain name and email as part of the email header. Many of these addresses were obtained from social engineering or were spoofing genuine domain names used by legitimate users.
Additionally, attacks that masquerade as internal communication can take advantage of employees\' curiosity about how DMARC works. The goal of DMARC is to protect employees from COVID-19, a malicious code injected into target organizations’ internal networks. Since then, hundreds of thousands of organizations have been protected against this emerging threat. Organizations can identify potential carbon copies of valid employee credentials in their network with just a few lines of code. By using an Industrial Rule of the Road (IRT) management application, an insider can be prevented from spoofing administrative access and gaining unauthorized access to company data or sensitive business activities.
Each of the domains on the list is:
1. Eligible for DMARC enforcement
2. Actively being spoofed in malicious, COVID- related campaigns
3. Carries a very low risk of blocking legitimate email
The domains, along with corresponding domain owners, are:
@who.org (World Health Organization)
@cdc.gov (Center for Disease Control and Prevention)
@hhs.gov (Department of Health and Human Services)
@treasury.gov (US Dept. of the Treasury)
@irs.gov (Internal Revenue Service)
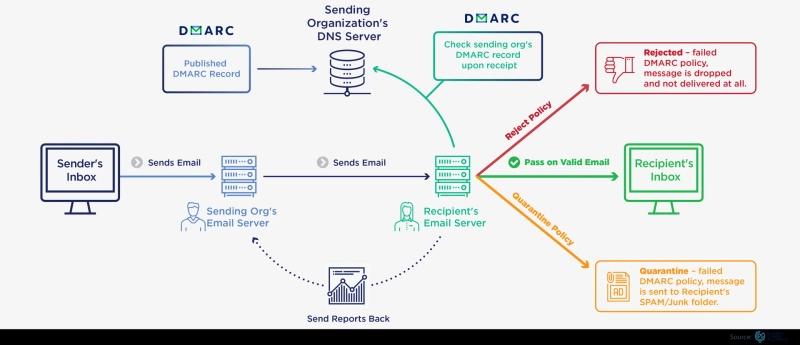
DMARC (Domain-based Message Access Protocol) is a solution that can be used to configure email gateways to deny access to unauthorized parties. By implementing DMARC, administrators are able to control who has access to their email inbox and domain. This in turn can help reduce spoofing of legitimate emails, data theft, and other attacks. As organizations continue to struggle with how to clamp down on spoofing and phishing attacks from sources inside and outside their networks, a new approach is needed. With today\'s malicious intent focused on obtaining personal identifying information from employees, organizations must be able to verify that employees are neither spoofing nor phishing from internal sources. This is precisely why expanded DMARC capabilities are important for organization security.
The most common attack vector being spoofing attack - where an outside party places an impersonating email address into the inbox of an individual who then forwards that email on to the intended recipient. This type of attack can also be prevented if DMARC is properly configured on the upstream email gateway system. The Configuring DMARC for E-mail GATEWAYS (CX) module is used by ISP providers to manage DMARC Registration and Integration on their end-to-end domain policies. The objective of this module is to correctly identify, for each incoming e-mail message, whether it is from a legitimate domain (MX), a spoof domain (SPF), or an Incorrect Domain (ID) challenge. On receiving such an alert, the configured DMARC policy validates the source of the e-mail message and indicates whether it should be handled as a spam or Not Spam message.
Source :-https://atozcybersecurity.blogspot.com/2021/09/how-dmarc-can-protect-employees-from.html