When it comes to cyberattacks, “Man in the middle” attacks occur quite commonly. It is also one of the oldest forms of cyberattack. To explain the nature of a man in the middle attack, here is an example-
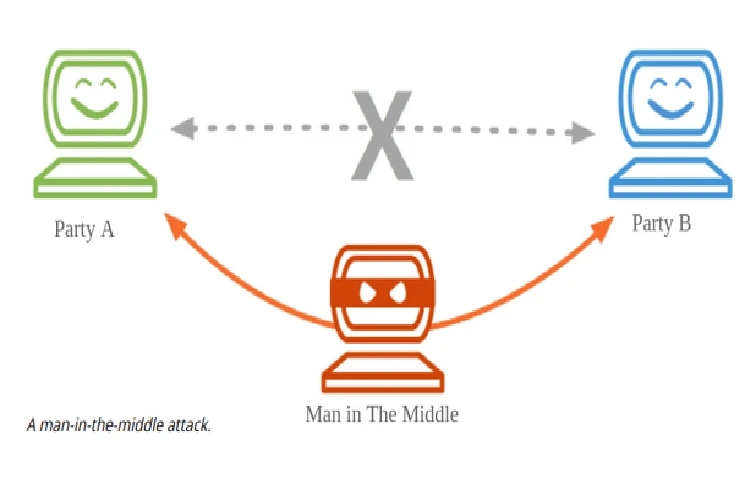
Supposedly, “A” & “B” are connected through a channel, and C snoops into the channel and pretends to be A for B and B for A, while both A & B are unaware of the intrusion of “C”. The commenced attack is known as session hijacking or eavesdropping attack.
The motive of the hacker is to collect confidential information by inserting themselves into channels they think, carry an exchange of conversations that might help them blackmail both the parties in any way.
In this blog, we will discuss MITM attacks and various methods of attacks & how to avoid them altogether.
What Is Man In The Middle Attack?
A man in the middle attack is when a hacker hacks an exchange channel between 2 parties unbeknownst to them, the hacker then pretends to be both the legitimate parties without any suspicion. The hacker then intercepts the information being exchanged between the parties. A more sinister hacker may even deploy malware to both the party’s systems and commence another cyberattack.
You can say that this attack is like a communication game, where the initial thing starts as something else and becomes something else as it reaches the target, passing through different mediums. The hacker is the “Different medium” who manipulates the exchange of conversation from both ends to get their hands on exclusive information or otherwise cause damage to both parties.
In the above diagram, you can see that the attacker places themselves between 2 parties or server & client to intercept the information that they are exchanging.
How Does The Man In The Middle Attack Take Place?
There are several methods of carrying out a MITM attack, one of the popular types is the automated attack. As per the SANS Institute, “There are tools to automate this that look for passwords and write it into a file whenever they see one, or they look to wait for particular requests like for downloads and send malicious traffic back.”
Although mostly the MITM attacks are WI-FI based hence they need proximity to be carried out, there are ways to carry them out remotely as well. Remote attacks are more sophisticated because they require remote routing.
Other than remote routing, DNS spoofing is also a method of MITM attack. The attacker will change the DNS (Domain Name System) setting, so, whenever you are visiting a particular website, you will end up connecting to the wrong IP address that is provided by the attacker. Once you are lured in, then the attacker will commence the Man In The Middle attack.
Another popular method of effectuating the MITM attack is through fake phone towers, e.g., the law enforcement department of Canada, US, and UK have used this method through tools called “Stingray”. They are fake phone towers. They use these devices to gather information.
How To Avoid Man In The Middle Attack?
The basic thing you can do to keep your network safe is to opt for TLS and SSL encryption. Multifactor authentication will add another layer of security to your network. TLS or transport layer security is an encryption type that makes sure that the packages being interchanged through the network layer, will be in the layer securely and won’t leave the layer at any cost.
Through different firewalls and layered encryption, MITM attacks can be avoided. Though the MITM attacks are not as common as malware or ransomware attacks, they have been around since the late 1980s. To avoid such attacks, make sure you have proper security packages and don’t visit any suspicious sites.
As an internet user, you can follow these simple steps to avoid MITM attacks
- Don’t try to connect to those Wi-Fi connections that are not password protected.
- If your browser says a website is unsecure, then don’t visit it.
- Log out of any application when it’s not in use.
- Don’t use any unknown internet source while making a sensitive transaction or accessing any sensitive information.
You can always reach out for the help and advice of cybersecurity professionals. Cybersecurity Companies will provide you with your network and system analysis to fish out vulnerabilities and provide suitable solutions accordingly.