Strengthening Your Cybersecurity with a Top-Notch Security Operations Center (SOC)
In the fast-paced and interconnected world of today, cybersecurity is of paramount importance. As businesses and organizations increasingly rely on digital technologies to manage their operations and store sensitive data, the threat landscape has also expanded. Hackers and malicious actors are constantly looking for vulnerabilities to exploit, putting your valuable assets at risk. To counter these threats effectively, you need a robust and proactive approach, and that’s where a Security Operations Center (SOC) comes into play.
What is a Security Operations Center (SOC)?
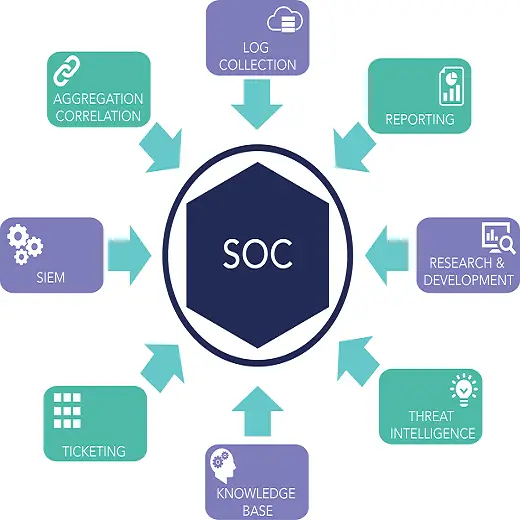
A Security Operations Center, commonly referred to as SOC, is a central hub within an organization that takes charge of monitoring, detecting, and responding to cybersecurity incidents. The primary objective of a SOC is to safeguard the company’s digital environment, including networks, systems, applications, and data, from potential threats and attacks. It serves as a critical line of defense, enabling organizations to stay one step ahead of cyber threats and mitigate risks effectively.
The Role of SOC in Strengthening Cybersecurity
1. Real-time Threat Monitoring and Detection
A well-established SOC employs cutting-edge technology and advanced security tools to monitor the organization’s digital infrastructure in real-time. By analyzing network traffic, system logs, and user behavior, the SOC can swiftly identify unusual activities and potential security breaches. Early detection allows security analysts to respond promptly and prevent the escalation of the threat.
2. Incident Response and Mitigation
When a potential threat is identified, the SOC team initiates an incident response plan. They follow predefined protocols to investigate the incident, assess the extent of the damage, and take appropriate measures to contain and mitigate the impact. Through their quick actions, the SOC minimizes the downtime and disruption to normal business operations.
3. Proactive Threat Hunting
In addition to real-time monitoring, a proactive SOC engages in threat hunting. This means actively searching for signs of potential threats that may have gone unnoticed by automated systems. By being proactive, the SOC can discover and neutralize emerging threats before they cause significant harm.
4. Security Intelligence and Analysis
A SOC accumulates vast amounts of security-related data over time. This information is invaluable in understanding the evolving threat landscape and identifying patterns or trends. The SOC analysts perform thorough analysis and provide actionable intelligence, helping organizations make informed decisions to enhance their cybersecurity posture.
Transitioning to a SOC: Key Considerations
Implementing a Security Operations Center requires careful planning and consideration. Here are some essential steps to ensure a smooth transition:
1. Identify Your Security Goals
Before setting up a SOC, clearly define your security objectives and priorities. Understanding your organization’s unique risks and vulnerabilities will help tailor the SOC’s capabilities to meet your specific needs.
2. Invest in Skilled Professionals
A SOC is only as effective as the team behind it. Recruit and train cybersecurity professionals with expertise in threat analysis, incident response, and security operations. Continuous training is crucial to keep up with the ever-evolving threat landscape.
3. Embrace Advanced Technologies
Leverage the power of cutting-edge cybersecurity tools and technologies to equip your SOC with the necessary capabilities. Automation and artificial intelligence can significantly enhance the SOC’s efficiency and accuracy in threat detection and response.
4. Foster Collaboration and Communication
Encourage seamless communication and collaboration between the SOC team and other departments within your organization. An integrated approach to cybersecurity ensures a swift response and a united front against cyber threats.
Conclusion: Bolstering Your Cyber Defenses
In conclusion, a Security Operations Center is a critical component of a robust cybersecurity strategy. By adopting a proactive approach to monitoring, detecting, and responding to cyber threats, a SOC empowers organizations to safeguard their digital assets effectively. Remember, cybersecurity is an ongoing process, and continuous improvement and adaptation are necessary to stay ahead in the ever-evolving cyber landscape. Invest in a well-structured SOC, and you’ll be taking a significant step towards protecting your organization from potential harm.
